Starting Course
After Intro
Section
Section
Section
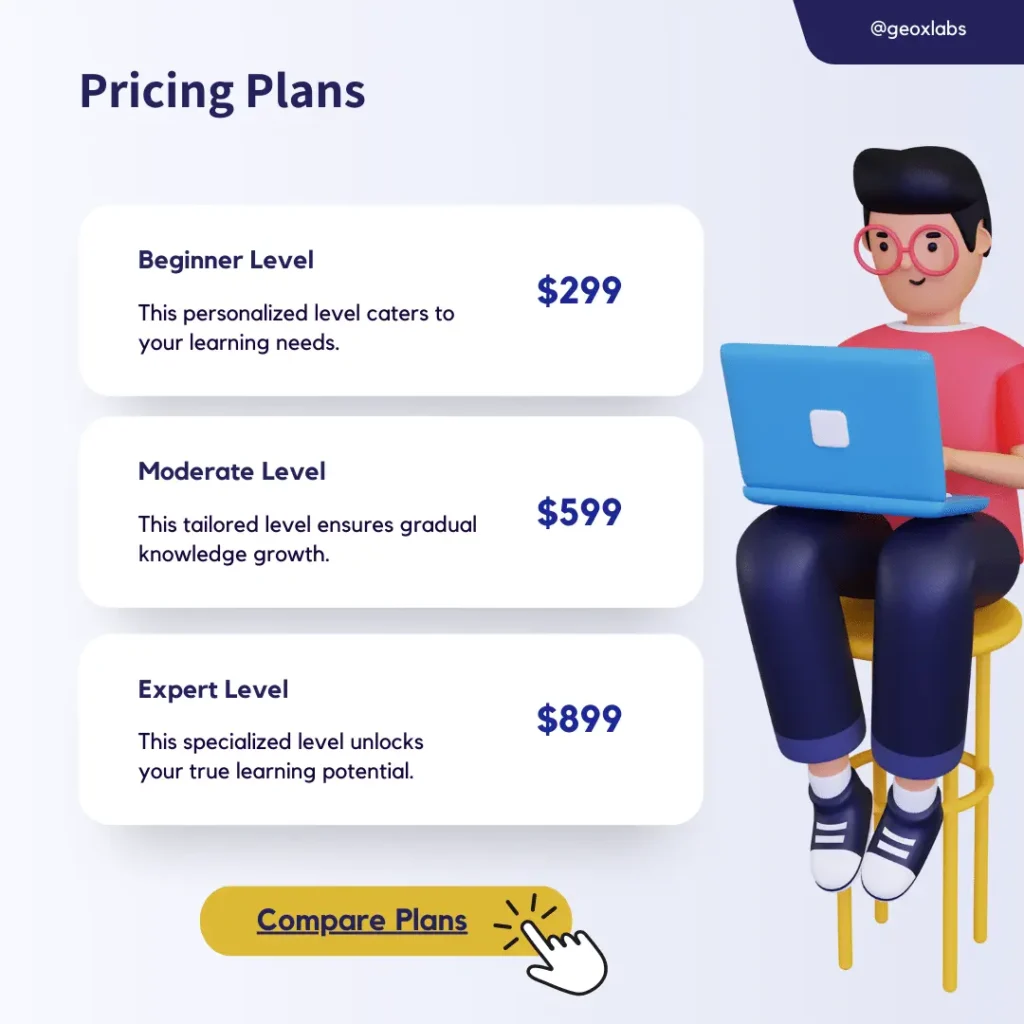
The duration of each course may vary. Please refer to the course details for specific information on the duration and pace of learning.
Our courses are designed to be flexible, allowing you to start at any time that suits you. There are no strict start dates, so you can enroll and begin learning whenever you're ready within a specified course completion period.
Yes, you will have continued access to the course material even after completing the course. You can revisit the content, review the lectures, and refer to the resources whenever you need them within a specified course completion period.
Yes, upon successfully completing the course, you will receive a certificate of completion. This certificate validates your participation and achievement and can be a valuable addition to your professional profile.
Prerequisites, if any, will be mentioned in the course details. Some courses may require a basic understanding of certain concepts or prior knowledge in a related field. However, our courses are designed to accommodate learners from various backgrounds.
We have a dedicated support team available to assist you throughout your learning journey. If you encounter any technical difficulties or have questions about the course content, you can reach out to our support team via email or through the learning management system (LMS). We have also created online breakout sessions with the course mentors and you can participate in such sessions.
Yes, interaction is encouraged! Depending on the course, you may have opportunities to engage with instructors and fellow participants through discussion forums, Q&A sessions, or live webinars. This collaborative learning environment allows for networking and sharing of insights and experiences.
Courses may include assessments or exams to gauge your understanding of the material. These assessments can take various forms, such as quizzes, assignments, or projects. They are designed to help reinforce your learning and provide valuable feedback.
Our refund policy may vary for different courses. Please refer to the enrollment details or contact our support team to inquire about the specific refund policy for the course you are interested in.
To enroll in a course, simply visit our website or the course page. There, you will find detailed information about the course, including the enrollment process, fees (if applicable), and any additional requirements. Follow the instructions.
Be the first to add a review.
Please, login to leave a review